Petya Ransomware
Does your company have a process in place to combat and/or react to a ransomware attack? If not, you should. The below article published on krebsonsecurity.com outlines one of the newest ransomware threats.
———–
A new strain of ransomware dubbed “Petya” is worming its way around the world with alarming speed. The malware is spreading using a vulnerability in Microsoft Windows that the software giant patched in March 2017 — the same bug that was exploited by the recent and prolific WannaCry ransomware strain.
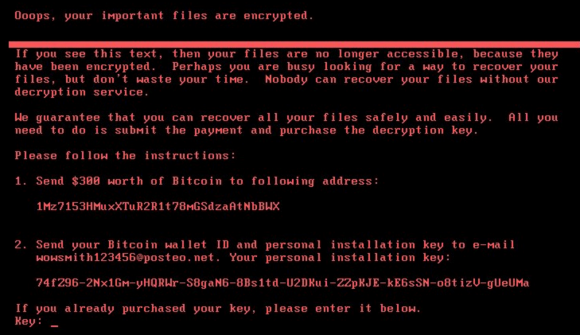
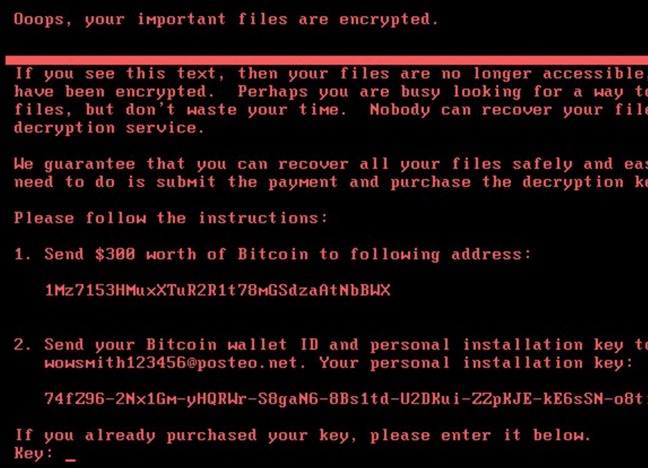
The ransom note that gets displayed on screens of Microsoft Windows computers infected with Petya.
According to multiple news reports, Ukraine appears to be among the hardest hit by Petya. The country’s government, some domestic banks and largest power companies all warned today that they were dealing with fallout from Petya infections.
Danish transport and energy firm Maersk said in a statement on its Web site that “We can confirm that Maersk IT systems are down across multiple sites and business units due to a cyber attack.” In addition, Russian energy giant Rosneft said on Twitter that it was facing a “powerful hacker attack.” However, neither company referenced ransomware or Petya.
Security firm Symantec confirmed that Petya uses the “Eternal Blue” exploit, a digital weapon that was believed to have been developed by the U.S. National Security Agency and in April 2017 leaked online by a hacker group calling itself the Shadow Brokers.
Microsoft released a patch for the Eternal Blue exploit in March (MS17-010), but many businesses put off installing the fix. Many of those that procrastinated were hit with the WannaCry ransomware attacks in May. U.S. intelligence agencies assess with medium confidence that WannaCry was the work of North Korean hackers.
Organizations and individuals who have not yet applied the Windows update for the Eternal Blue exploit should patch now. However, there are indications that Petya may have other tricks up its sleeve to spread inside of large networks.
Russian security firm Group-IB reports that Petya bundles a tool called “LSADump,” which can gather passwords and credential data from Windows computers and domain controllers on the network.
Petya seems to be primarily impacting organizations in Europe, however the malware is starting to show up in the United States. Legal Week reports that global law firm DLA Piper has experienced issues with its systems in the U.S. as a result of the outbreak.
Through its twitter account, the Ukrainian Cyber Police said the attack appears to have been seeded through a software update mechanism built into M.E.Doc, an accounting program that companies working with the Ukranian government need to use.
Nicholas Weaver, a security researcher at the International Computer Science Institute and a lecturer at UC Berkeley, said Petya appears to have been well engineered to be destructive while masquerading as a ransomware strain.
Weaver noted that Petya’s ransom note includes the same Bitcoin address for every victim, whereas most ransomware strains create a custom Bitcoin payment address for each victim.
Also, he said, Petya urges victims to communicate with the extortionists via an email address, while the majority of ransomware strains require victims who wish to pay or communicate with the attackers to use Tor, a global anonymity network that can be used to host Web sites which can be very difficult to take down.
“I’m willing to say with at least moderate confidence that this was a deliberate, malicious, destructive attack or perhaps a test disguised as ransomware,” Weaver said. “The best way to put it is that Petya’s payment infrastructure is a fecal theater.”
Ransomware encrypts important documents and files on infected computers and then demands a ransom (usually in Bitcoin) for a digital key needed to unlock the files. With most ransomware strains, victims who do not have recent backups of their files are faced with a decision to either pay the ransom or kiss their files goodbye.
Ransomware attacks like Petya have become such a common pestilence that many companies are now reportedly stockpiling Bitcoin in case they need to quickly unlock files that are being held hostage by ransomware.
Security experts warn that Petya and other ransomware strains will continue to proliferate as long as companies delay patching and fail to develop a robust response plan for dealing with ransomware infestations.
According to ISACA, a nonprofit that advocates for professionals involved in information security, assurance, risk management and governance, 62 percent of organizations surveyed recently reported experiencing ransomware in 2016, but only 53 percent said they had a formal process in place to address it.
Join the Conversation on Linkedin | About PEO Compass
The PEO Compass is a friendly convergence of professionals and friends in the PEO industry sharing insights, ideas and intelligence to make us all better.
All writers specialize in Professional Employer Organization (PEO) business services such as Workers Compensation, Mergers & Acquisitions, Data Management, Employment Practices Liability (EPLI), Cyber Liability Insurance, Health Insurance, Occupational Accident Insurance, Business Insurance, Client Company, Casualty Insurance, Disability Insurance and more.
To contact a PEO expert, please visit Libertate Insurance Services, LLC and RiskMD.